Sector coupling potential demands secure communications
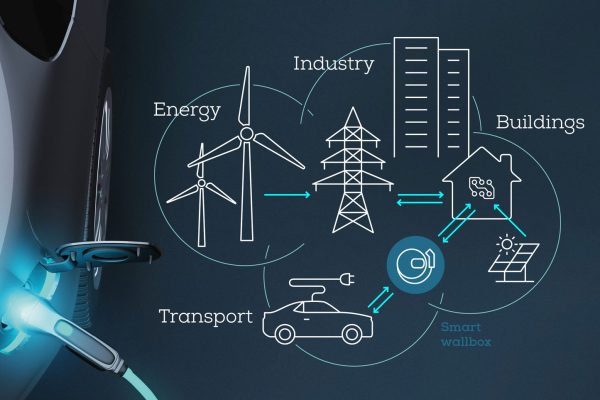
Beyond reductions in local air pollution and fossil fuel consumption, EVs could also make an important contribution to societal energy efficiency through participation in sector coupling. This is the integration and coordination of different energy sectors – such as electricity, heating, cooling and transport – with the goal of optimising the use of renewable energy sources and improving overall energy efficiency across all of those sectors. Realising this, however, will require the establishment and maintenance of secure communications at low cost, and that is a major challenge, as Alexander Bourgett, vice-president of strategic development and research at eSystems MTG in Germany, explains to Peter Donaldson.
The company works with automotive OEMs in key areas linked to e-mobility, including bi-directional smart charging and embedded computing.
EVs fit into sector coupling in three main ways. The first is smart charging, often referred to as V1G, which can help to reduce peak power demand on the grid and improve system flexibility. The second is vehicle-to-grid (V2G), which can help through peak shaving (providing extra energy at times of high demand), reducing network outages, providing support for mini-grids and accommodating more variable renewables. The third way is vehicle-to-building (V2B) provision in which the EV provides buildings with supplemental power.
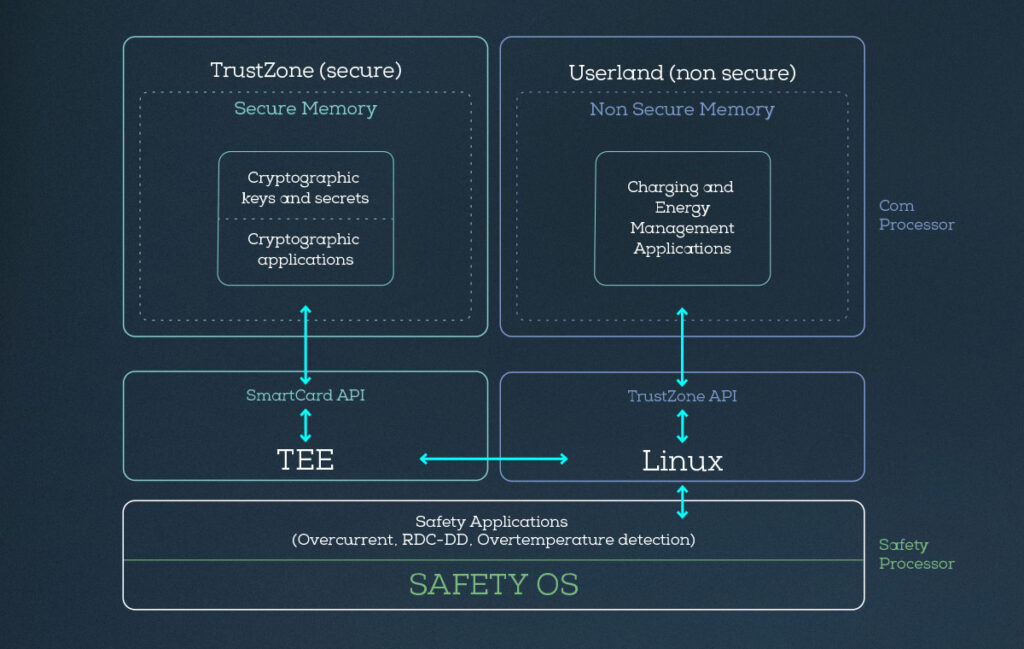
(Image courtesy of E-Systems)
Highly dynamic charging
“The charging process can be highly dynamic,” Bourgett says. “The car doesn’t have to be charged full-power all the time and it can be easily throttled.”
This, he adds can help by reducing the power that cars take from the grid at times of high demand, and by peak shaving the consumption of industrial facilities that pay according to the peak power made available to them – energy providers bill them extra if the peak load exceeds its normal level.
Further, the charging process can be optimised to make the most of local power generation, such as solar PV arrays, to minimise the power drawn from the grid. This means vehicle-charging systems must communicate with the local PV systems to ensure they only draw as many kilowatts as are available from the solar arrays or other local sources, Bourgett explains.
“It needs local energy management and can make use of dynamic tariffs,” he says. These are electricity pricing structures that vary, based on the time of day, week or season, to reflect the changing costs of electricity production. “And then, everything is about data communication. We need sensor data, data from solar forecasts, and we need grid congestion information.”
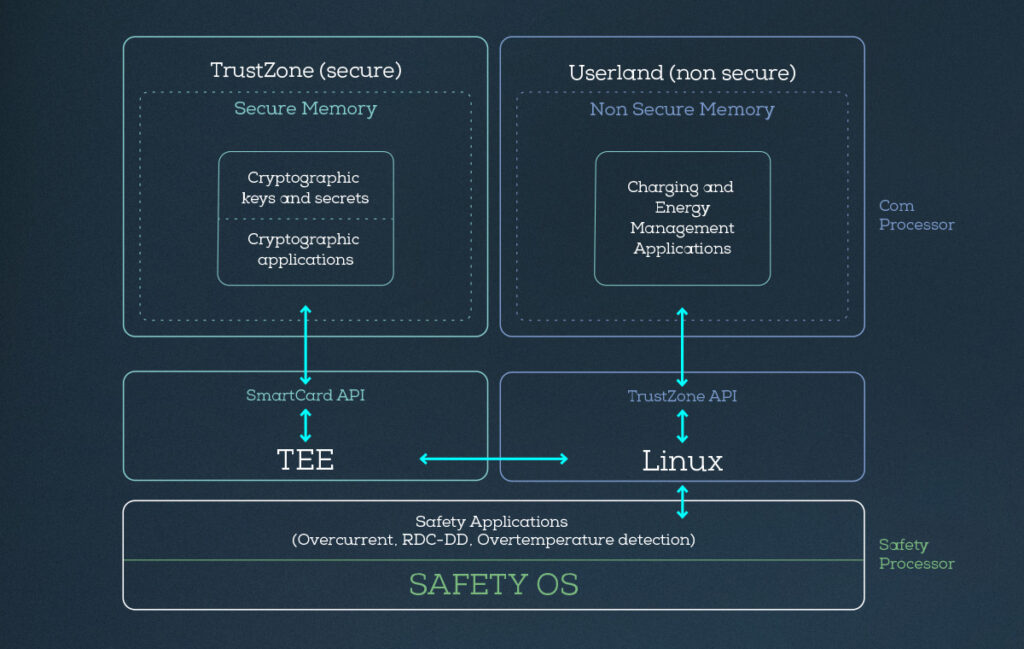
(Image courtesy of E-Systems)
Power needs
The system also needs to exchange data with the car, regarding the power needs of the grid over the next eight to 10 hours, when the car needs to be fully charged by and the battery’s present state of charge, for example, and to provide the car with price tables for the coming hours so that it can do its own calculations. If a domestic charger is used, then the home energy management system has to be consulted to ensure the car does not draw too much power etc.
This requires many protocols, such as the European EEBus standard and the Open Charge Point Protocol (OCPP), for example, along with models for energy meters, grid communication protocols such as OpenADR, and IEC standards in the European grid. There are also gateways that translate between local and grid protocols, Bourgett explains, with many combinations and variations around the world.
“In Germany, we have around 900 different definitions on how to connect your home to the local grid because we have 900 different grid providers. The good thing is that the standards bodies of the EU have understood that this is an issue. Now, we have to technically define the problem and harmonise; otherwise there will be so many different products for every market and nobody will pay to develop this stuff,” he says. “There are commercial interests and intellectual property issues that can only be dealt with by regulation.”
From eSystems’ perspective as a wall-box charger supplier, the quickest way to provide benefits to EV drivers is to work with local energy providers offering dynamic tariffs. “This is the fastest path because we do not have to deal with the full grid.”
Cyber security
In addition to harmonisation, the other big issue that must be tackled to make the most of sector coupling and smart charging in such critical infrastructure is cyber security.
“Your hardware has to provide a means to secure your communications,” Bourgett says. “You have to prevent man-in-the-middle and distributed denial-of-service attacks, and stop unauthorised actors from reading your data.” Without such protections, attackers could destabilise the grid.
“The architecture of the systems has to be more secure,” he says. “It cannot run on hacked-together Raspberry Pis with USB sticks running the charging systems. There have to be more mechanisms to boot and run systems securely so they can’t be controlled by some rogue back-end system somewhere.
“If you look at some wall boxes, the wiring is hacked together by some manual process, and there are some controllers that can be updated by inserting a USB stick with a text file, and you can read the password, which might be the same for 50,000 boxes. This has to change.”
The problem, Bourgett argues, is not the technology but the commercial model: “If you talk to providers of identity management systems for online banking, for example, they always have a one-to-one relationship with the customer. You have your PC and your smartphone, and you are happy to pay four euros a month for your bank account, but if you have a wall box maybe running for seven years before it shows a defect you won’t pay four euros a month. The things have to get cheaper.”
High-performance hardware
This is why the security of such systems is heavily dependent on hardware architecture. Today, eSystems is using the same kind of high-performance chips found in automotive and embedded computers. The company is focused on deploying secure platforms and is on its second generation of systems that rely on the TrustZone security architecture on ARM processors.
A hardware-based feature, TrustZone, is designed to provide a secure execution environment to enable the coexistence of secure and non-secure software on the same device while isolating them from each other.
“This is a technology that comes from the smartphone world,” Bourgett says. “It’s not new, but implementation takes some knowledge, and microprocessor manufacturers increasingly offer these features.”
He notes that the company does its own penetration testing on its wall boxes and has independent auditors checking the security of its architecture.
“It implements read-only and block-based encrypted or signed data on our flash system,” he adds. “We have fully encrypted communication channels with TLS, and we have specific and signed certificates for every connection. The certificates have expiry dates, and we have update mechanisms for them, and we even have root certificates for bank account communications.”
This should position the company well for an upcoming change in European regulations, due to come into force in 2024-25. This will require all wireless devices connected to the internet to meet the cybersecurity requirements set out in the EU Radio Equipment Directive (RED).
“If you sell a product in Europe, you will have to show cybersecurity tests and results,” Bourgett says.
Having been preparing for this for three years, the company is now ready with its ghostOne wall boxes. “If you integrate security from the start, it is relatively easy, but if you try to add it on later, you’re failing,” he concludes.
ONLINE PARTNERS