EV charger security vulnerability
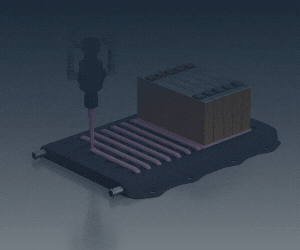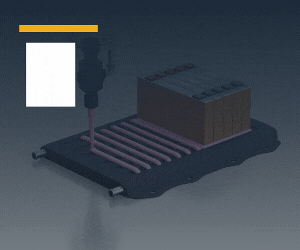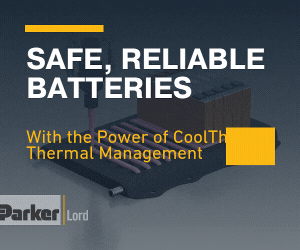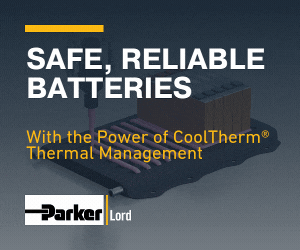
(Image: SwRI)
Researchers in the US have identified a security vulnerability in a standard protocol governing communications between electric vehicles (EVs) and EV charging equipment, writes Nick Flaherty.
The research has prompted the Cybersecurity & Infrastructure Security Agency (CISA) to issue a security advisory related to the ISO 15118 vehicle-to-grid communications standard as a Common Vulnerabilities & Exposures (CVE) advisory.
The researchers at the Southwest Research Institute (SwRI) spoofed signal measurements between an EV and EV supply equipment (EVSE) using both a wired and a wireless connection.
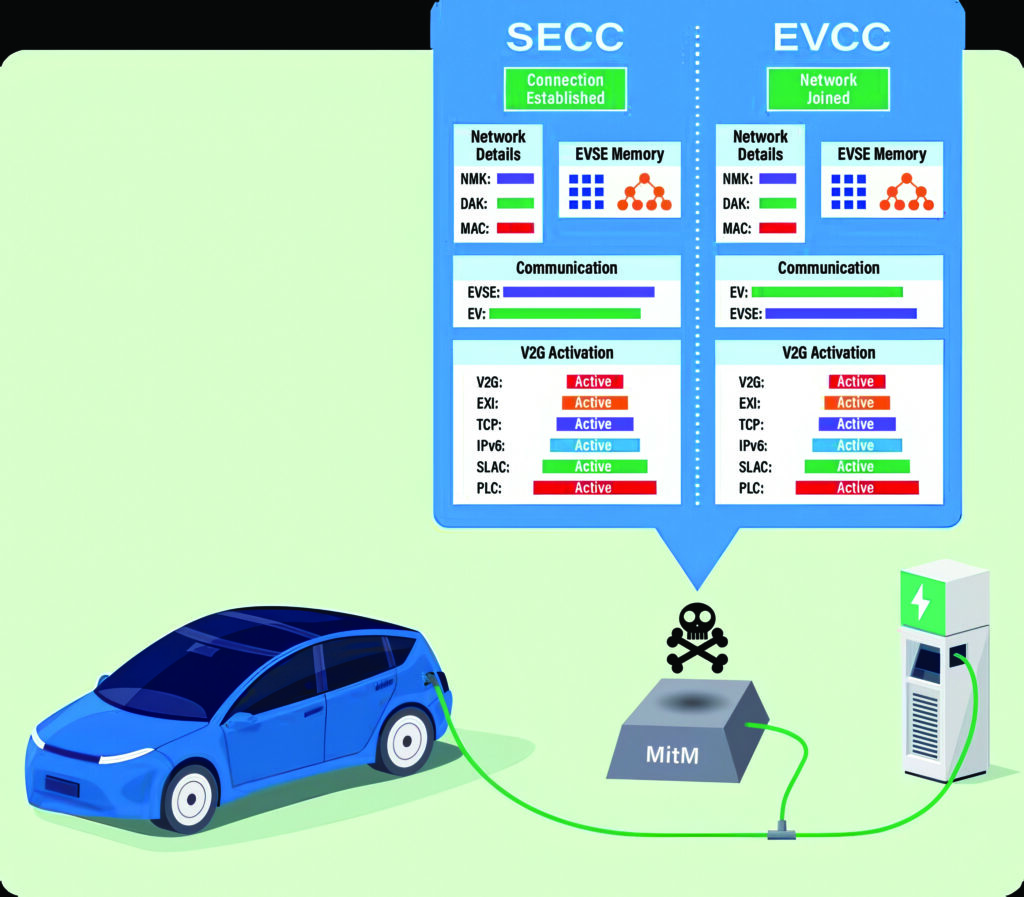
The SwRI team reverse-engineered the signals and circuits on an EV and a J1772 charger, the most common interface for managing EV charging in North America. They successfully disrupted vehicle charging with a spoofing device developed in a laboratory using low-cost hardware and software.
The research explored vulnerabilities in the Signal Level Attenuation Characterization (SLAC) protocol. The ISO 15118 communication standard relies on SLAC to identify which charging station a particular vehicle is connected to within a charger network.
After identifying security deficiencies within the SLAC process, SwRI’s research team developed a machine-in-the-middle (MitM) attack, and then modelled the attack using simulators before replicating the attack between vehicles and charging stations.
The MitM attack demonstrated that the EV charging process could be manipulated or halted. The researchers also drained the battery and generated signals to simulate J1772 charging rates.
“It took some time to develop the software for the attack, but running the attack was surprisingly consistent,” said Kyle Owens, an engineer who supported the project. “The research demonstrates how a malicious actor can trick an EV into establishing a connection by responding to the vehicle’s SLAC signal with an artificial measurement.”
“The project effectively tricked the test vehicle into thinking it was fully charged and also blocked it from taking a full charge,” Dodson said. “This type of malicious attack can cause more disruption at scale.”
SwRI also performed two other manipulations: limiting the rate of charging and blocking battery charging and overcharging. When overcharging, the vehicle’s battery management system detected a power level that was too high and automatically disconnected from charging.
The research focused on J1772 Level 2 chargers, with tests planned for Level 3 chargers and penetration of other devices used on fleet vehicles and electric scooters.
Click here to read the latest issue of E-Mobility Engineering.
ONLINE PARTNERS